
A treasure trove of personal data including emails and unecrypted passwords has been found up for sale on the Dark Web.
The discovery of over 1.4 billion identifying documents is thought to be the largest yet recorded, according to security experts in the US.
The Dark Web consists of sites which don’t appear in Google or other public search rankings, but anyone with access can work around restrictions on content filtering, illegal or shady practices or out-and-out criminality, such as selling weapons, stolen goods, drugs and more.
In a Medium post, 4iQ researcher Julio Casal asks: “Is the cybercrime epidemic about to become exponentially worse?”
Casal reports that while 4iQ was scanning the deep web and Dark Web for stolen, leaked or lost data, it discovered a single file containing a database of 1.4 billion “clear text credentials”.
That’s pairs of usernames and clearly visible passwords. 1,400,553,869 of them.
How stolen details work
The information on the database is interactive and searchable – taking away most of the difficult deciphering work usually involved in buying stolen details.
Often data is dumped on the Dark Web in list format. Often it’s not easily searchable nor is it able to take on new imported data, making hard yards for hackers as they scramble to turn the information into something they can quickly and easily exploit.
More: Do I need a password manager?
Casal writes: “Since the data is alphabetically organized, the massive problem of password reuse — same or very similar passwords for different accounts — appears constantly and is easily detectable.
“Given the fact that people reuse passwords across their email, social media, e-commerce, banking and work accounts, hackers can automate account hijacking or account takeover.
“This database makes finding passwords faster and easier than ever before. As an example searching for ‘admin’, ‘administrator’ and ‘root’ returned 226,631 passwords of admin users in a few seconds.
“None of the passwords are encrypted, and what’s scary is the we’ve tested a subset of these passwords and most of the have been verified to be true.”
Because the database is easy to use, even unsophisticated or first-time hackers will be able to access it.
Password trends; passwords reused
And because it’s helpfully organised alphabetically, it offers concrete examples on how people tend to set their passwords, reuse them and create repeating patterns over time.
When 4iQ informed some of the people listed in this breach, they said the most common reaction is: “But that’s an old password”, commonly followed by, “Oh my! I still use that password in
How big and bad is it?
Although the majority of these breaches are apparently well known to the hacker community, 14% of exposed usernames and passwords had not been seen or decrypted before and are now available in clear text.
The breach is nearly twice as large as the previous biggest data exposure, the Exploit.in combo list that revealed 797 million records.
The data here combined everything from 252 previous breaches, including decrypted passwords from the Linkedin hack in 2013. Around 41GB in total was discovered in early December in what 4iQ say is an “underground community forum”.
Often data is stolen and hawked around on sites we might already be familiar with, like Reddit, with hackers taking payment in untraceable cryptocurrency such as Bitcoin.
What to do now
The key thing for anyone reading this article is to find out if your personal details have been exposed.
Microsoft Regional Director and security expert Troy Hunt runs a free service called HaveIBeenPwned.com.
Running since 2013, the tool allows you to search your own personal email addresses and passwords to see if they have ever been exposed online.
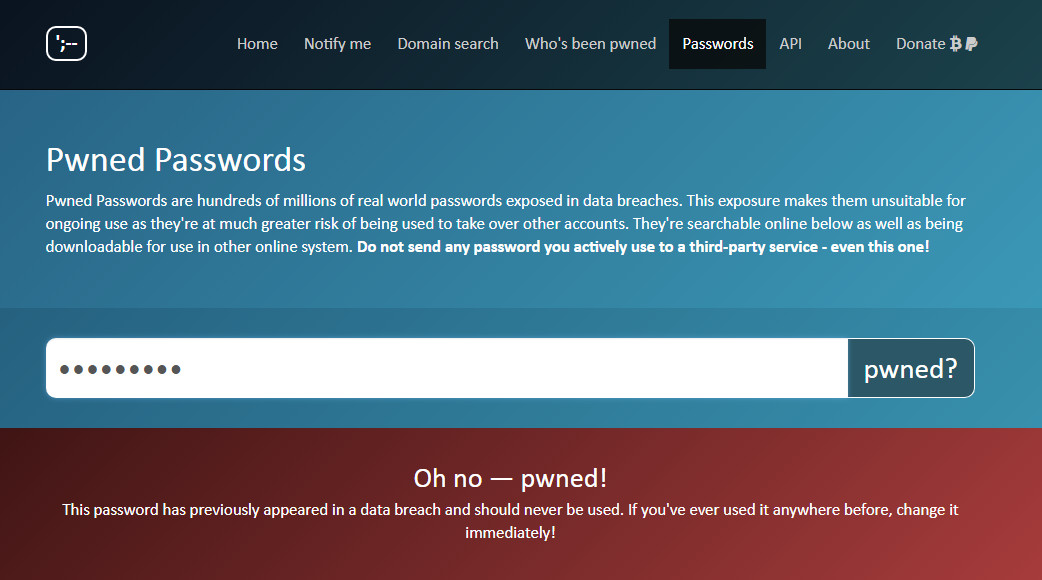
– Enter your most common passwords in the box at HaveIBeenPwned.com/Passwords and you’ll see whether this password appears in any of the most common data breaches since 2013.
– If you’ve been affected, login to the exposed accounts and change your password
– Try to set up two-factor authentication (so a phone number or other email address linked to your account)
– Be wary of any approaches made to you asking for ransoms and report everything to Action Fraud, the UK’s centre for online and cyber fraud.