Are ad blockers safe to use?
Posted 23rd October, 2018 @ 11:30 am | by Neil Cumins | inGuides
The decline of print journalism has led to a corresponding decrease in print advertising revenue.
The sale price of newspapers and magazines has only ever covered a proportion of their total production costs.
Print media has always relied heavily on advertising to stay solvent – which is a problem for online versions of those publications, or websites with no income from hard copy sales.
Without firewalling websites exclusively for paying customers, running costs have to be covered with a combination of sponsorship and advertising.
For the advertisers themselves, discreet static banner adverts don’t really attract sufficient attention any more.
This has led to increasingly obtrusive pop-up adverts appearing online, in tandem with screen-filling interstitials which obscure or grey out page contents until they’re closed.
No colour is too bold, no font is too large and no “click to close” box is too discreet.
Some websites increasingly resemble an online version of New York’s Times Square, with an array of flashing neon banner ads and autoplaying embedded video clips.
The latter are socially embarrassing when their audio soundtracks unexpectedly explode into life, a moment after the page has loaded.
Frantically trying to close the offending media file (or find a Mute button) is one of the modern day internet’s less welcome phenomena.
Fighting back against intruders
The obvious solution is to use specialist software to block aggressive and antisocial advertising techniques.
Ad blocker tools are readily available from app stores, freeing us from the tyranny of interstitials and hover ads.
But are they safe to use, and is there a moral argument against them?
Are ad blockers safe?
Not only are they perfectly fine for daily use, they might actually improve device security.
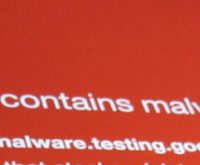
Adverts are coded separately to page content, making it relatively easy for criminals to hide malware in them before they begin displaying in a browser window.
It isn’t even necessary to click on the adverts for a device to be compromised.
Are there other benefits?
Web copy is far easier to read if it’s not surrounded by lurid “you might also like” clickbait articles, or images accompanying “sponsored links”.
This helps to keep people on a particular website for longer, with positive benefits when Google and Bing calculate search engine optimisation rankings.
Pages will load and display more quickly (which also benefits SEO), while consuming far less data.
Up to 50 per cent of data on some news platforms is advertising rather than editorial, yet every last byte needs to be downloaded onto each consumer device.
For anyone connected via 4G rather than WiFi, a significant amount of monthly data will be used to display unwanted (and often irrelevant) content.
Are there any drawbacks to blocking adverts online?
Because they’re relatively blunt instruments, ad blockers frequently prevent legitimate content from displaying.
This could potentially derail ecommerce transactions, unless these sites are whitelisted in advance as being allowed to display pop-ups or banner messages.
Some ad blockers recoup their own development costs by agreeing deals with online advertising platforms, ensuring certain adverts get through.
Others cover their coding and marketing budgets by – and this might sound familiar – monitoring your online activities before selling this data to third parties for advertising.
Also, sites like YouTube will refuse to display any content if ad-blocking software is detected.
It’s important to research any ad blocker carefully, before installing it.
Is this software ethical?
This is a much harder question, since it boils down to whether you’re willing to pay for online content.
After all, newspapers and magazines were rarely handed out for free until Shortlist and Metro came along.
We only get to access Facebook for free because sophisticated algorithms are monitoring our online activities, selling personal user data to advertising firms.
Unlike social media platforms, commercial websites like Buzzfeed and Rock Sound require large volumes of original content producing every week by skilled professionals.
It’s easy to forget how many graphic designers, publishers and journalists are involved in producing media content – all needing payment for their time and skills.
If ad blockers continue to damage online advertising income streams, content will either disappear entirely or be moved behind a paywall.
And since online advertising tools monitor how frequently ads are displayed, not using an ad blocker might help to stave off the day when the internet is no longer free to use.
It could also prevent websites without an alternative income stream from going out of business, which would be regrettable for owners, employees and audiences alike.